Mascot Security: sharing search results
How can you share Mascot result reports with external colleagues or customers? The most flexible solution is to use Mascot security to provide external users with limited access to your Mascot Server.
Mascot Security is a role-based access system. Rights to perform particular actions, such as run a search, are assigned to a group. Users gain rights by belonging to one or more groups. The idea is to make administration simpler, because you apply changes to the group, not to every user who belongs to the group. The full details are in chapter 12 of the Installation & Setup manual.
HTTP(S) access
In a typical configuration, external users need to be able to view their own result reports, but not those of other people, and they wouldn’t be able to submit new searches.
The only tricky aspect is enabling external access to your Mascot Server without compromising security. If you work in a large organisation with well developed IT policies, external access will be either allowed or forbidden. If it is allowed, there will be systems in place. The important aspect to emphasise to your IT contact is that you only want to open up HTTP (port 80) or HTTPS (port 443) access to the Mascot Server; nothing else is required.
If your IT environment is more do-it-yourself, the simplest and safest option is to open up port 80 on your Mascot Server through the firewall between your LAN and the Internet in a highly restricted fashion. Any decent firewall will allow you to create an inbound rule for port 80 that specifies both the external and internal IP addresses. That is, the external user will only be able to connect to the Mascot web server and only from a specified IP address. You’ll have to ask each external user for their IP address. If they aren’t sure what it is, there are many web sites that will tell them, such as whatismyipaddress.com.
If you want to live dangerously, and open up port 80 to any external IP address, you need to take a lot more care with security. Malicious people will try to gain control of the machine, often via weaknesses in the web server software, so you have to know what you are doing. Assuming you have the expertise to lock down the machine, it is essential that Mascot security is enabled with secure passwords and the guest account disabled.
Creating an external group
If Mascot security is not enabled, you have to enable it as described in Chapter 12 of the Mascot Server Installation and Setup manual. From that point onwards, everything is handled through a web browser.
First, you must log in as admin and change the administrator password. Then, you can create and edit users and groups. The default PowerUsers group will often be appropriate for people working in the lab. The default Daemons group contains the access rights needed by client software such as Mascot Daemon and Mascot Distiller.
In the simplest case, you want an external user to be able to view their own result reports, but not those of other people, and they shouldn’t be able to submit searches. These would be suitable settings for the group:
SEARCH: Allow all fasta databases to be searched
VIEW: Allow user to view the search log
The first setting is required because reports sometimes need to retrieve information from the Fasta file, such as the protein sequence for a Protein View report. The second setting allows the external user to browse their searches in the Mascot search log, where they will only see their own searches, not those for any other user.
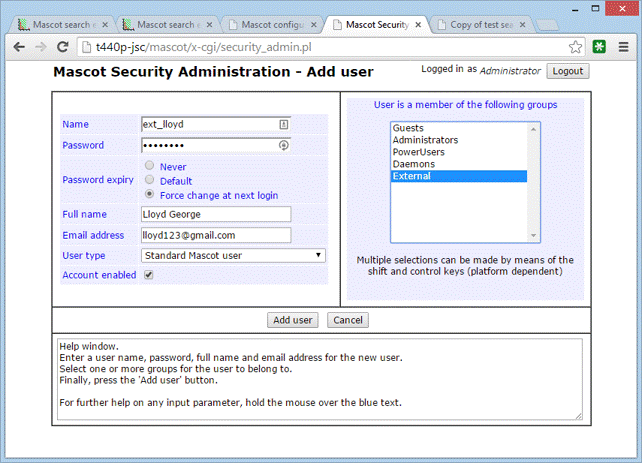
Assume we call this group ‘External’. Now, we add a new user and make them a member of the External group. Best to create an initial password and tell them what it is, but also select Force change at next login. The create user form in the security administration utility would look something like this:
Don’t forget to create a new rule in your firewall for the new user’s IP address.
Running searches as external users
How do you run searches for this user, since they are not allowed to run searches themselves? If you look at the security settings for the deamon user, you’ll see CLIENT: For Mascot Daemon, allow spoofing of another user. This allows a user logged in as a member of the this group to impersonate any other user. You can use the browser-based search forms, or Mascot Distiller, but it is often more convenient to use Mascot Daemon. If Daemon is logged in as a member of a group with the spoofing right, at the top left of the task editor tab, you’ll see a dropdown list of users. Simply select the appropriate user before running the task.
Allowing external users to see each other’s results
Adding individual external users, who only need to see their own results, to the same security group works fine. But, what if external users want to have access to each other’s results? For example, imagine you run samples for Bill and Ben at Garden City University, and Bill and Ben want separate logins but need to see each other’s results. To do this, you need to create a dedicated group, say Ext_garden_city with these rights:
SEARCH: Allow all fasta databases to be searched
VIEW: Allow user to view the search log
VIEW: See search results from other people in your own group
Bill and Ben (and any future members of this group) will then be able to see each others results, but not those of members of any other group.
Mascot security offers fine grained control of all aspects of using Mascot. For example, you can specify that a particular database is private to a group. You can even have private variable modifications. For users allowed to submit searches, you can control the types of search available, and set limits on the number of spectra and the execution time. You can allow viewing of configuration files and, if you really trust someone, allow them to edit configuration files.
If you have a very large number of users, there are scripts to add groups and users at the command line. The best sources of further information are Chapter 12 of the Mascot Server Installation and Setup manual (linked from your local Mascot home page) and the final module of the training course.